IDENTIFY ATTACKERS IN ACTION
Attackers are becoming more sophisticated and the techniques they use are much stealthier, harder to detect, and take increasingly longer to remediate.
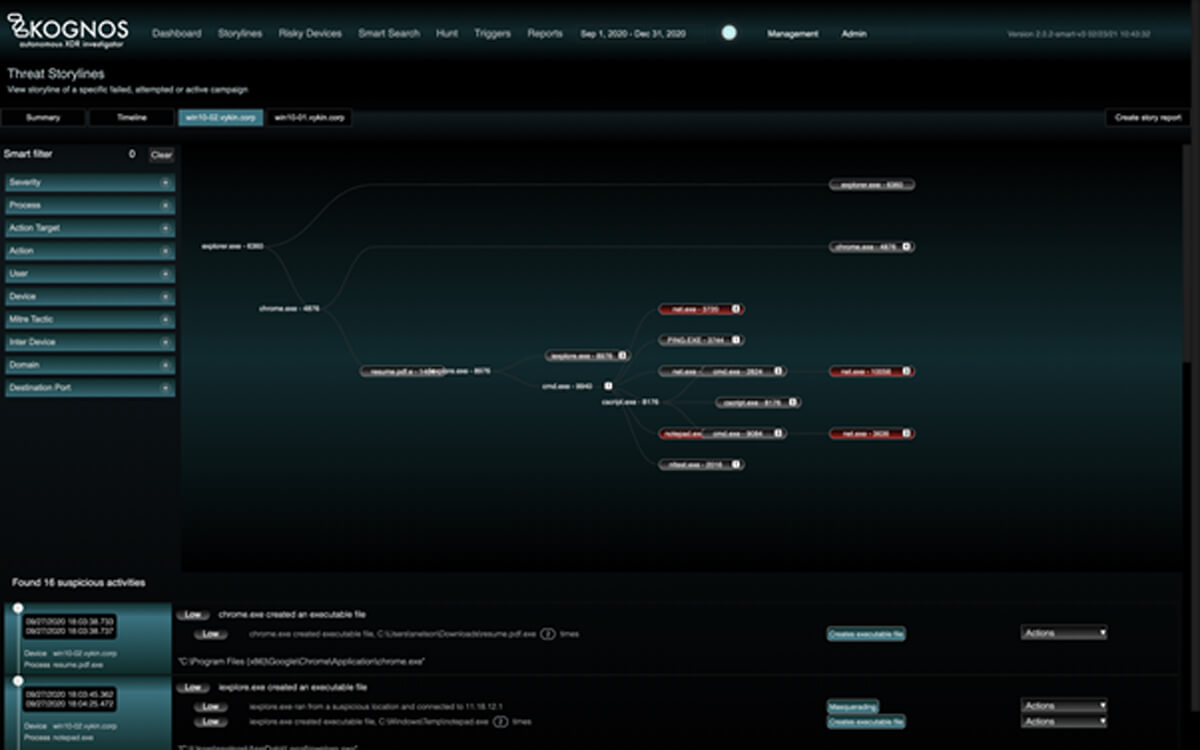
By autonomously forging relationships between event data coming from an organization’s existing telemetry sources, the Kognos XDR Investigator is the only solution that allows organizations to trace laterally moving campaigns, living off the land binaries, and insider threats–regardless of if they are active campaigns, attempted campaigns, or failed campaigns.
Insider Threats
Malicious insiders are one of the hardest groups of adversaries to detect. They are inside your environment and can blend in with the rest of the users. Firewalls and IDS products are often deployed at the perimeters of an enterprise and are completely blind to people who are already inside and using the infrastructure legitimately.
Malicious insiders could be current and former employees, contractors, partners or service providers who have/had a legitimate reason for using the infrastructure, but have malicious intent.
What Malicious Insiders Do:
Financial gain is a primary motivator for a majority of insider threats. These adversaries typically focus on exfiltrating intellectual property, employee information, customer data and other valuable information. Disgruntled employees might also delve into data destruction, defacement or other destructive activities.
Kognos platform is built to trace the subtlest of suspicious behavior. Given we are tracing the entire activity of the user, we can cumulatively look at the insider’s activity to bubble up possible threats. Use of abnormal tools, excessive movement of data, abnormal use of external domains are all traced by the Kognos platform.
The Kognos XDR Investigator autonomously forges relationships between event data coming from an organization’s existing telemetry source to trace the attackers path, hunt down suspicious activity, and investigate the chain of events to identify the complete attack campaign.