IDENTIFY ATTACKERS IN ACTION
Attackers are becoming more sophisticated and the techniques they use are much stealthier, harder to detect, and take increasingly longer to remediate.
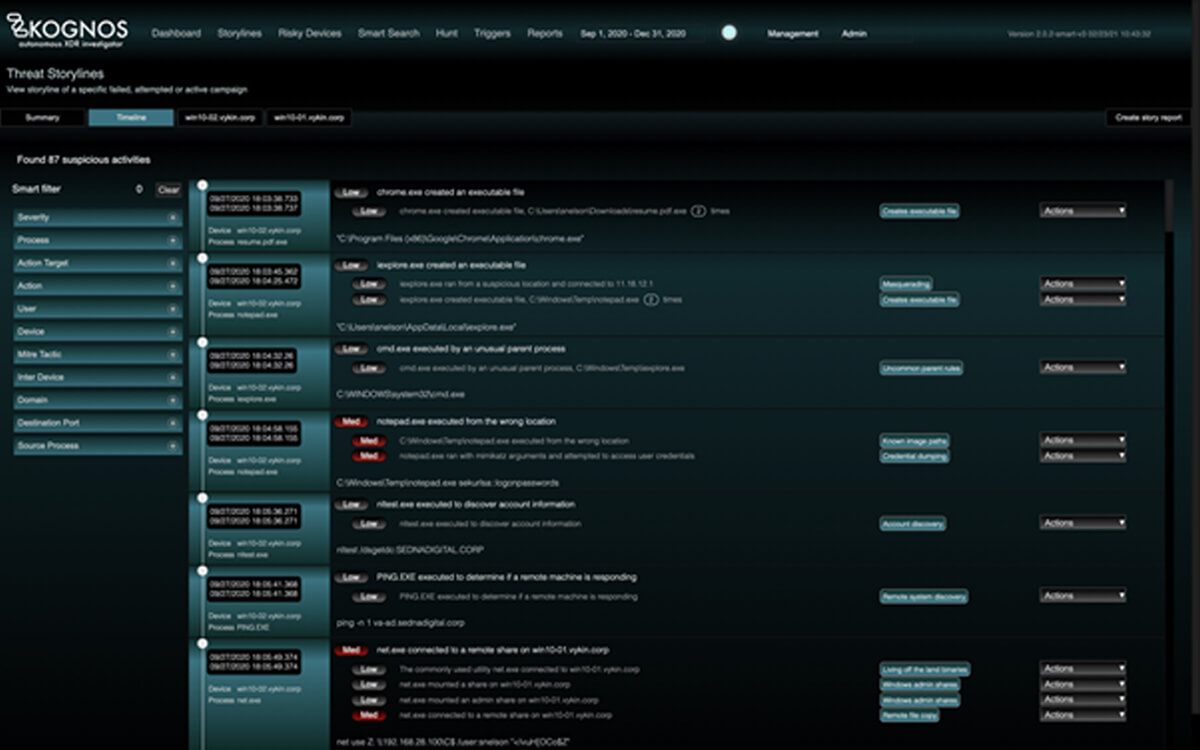
By autonomously forging relationships between event data coming from an organization’s existing telemetry sources, the Kognos XDR Investigator is the only solution that allows organizations to trace laterally moving campaigns, living off the land binaries, and insider threats–regardless of if they are active campaigns, attempted campaigns, or failed campaigns.
Living off the Land Binaries
Living off the land is a technique that’s been in use in the past – but is becoming prevalent amongst sophisticated adversaries to stay under the radar as much as possible. In these cases, the attackers are using legitimate binaries native to the operating systems for various nefarious purposes to evade detection.
What an attacker can do living off the land binaries:
LoTL binaries can be used by attackers for a plethora of tactics and techniques, including:
- Executing code as in PowerShell or VB scripts of WMI
- Credential dumping with tools like procdump
- Scheduling jobs with Task Scheduler
- Modifying registry keys
- Copying or moving files
- …and the list goes on and on
Given that most of these tools are also used for legitimate purposes, it becomes extremely hard for most detection systems to discriminate against such behavior. Kognos uses the power of relationships to look at the suspicious use of these binaries cumulatively to detect even the subtlest of attacks with great accuracy.