IDENTIFY ATTACKERS IN ACTION
Attackers are becoming more sophisticated and the techniques they use are much stealthier, harder to detect, and take increasingly longer to remediate.
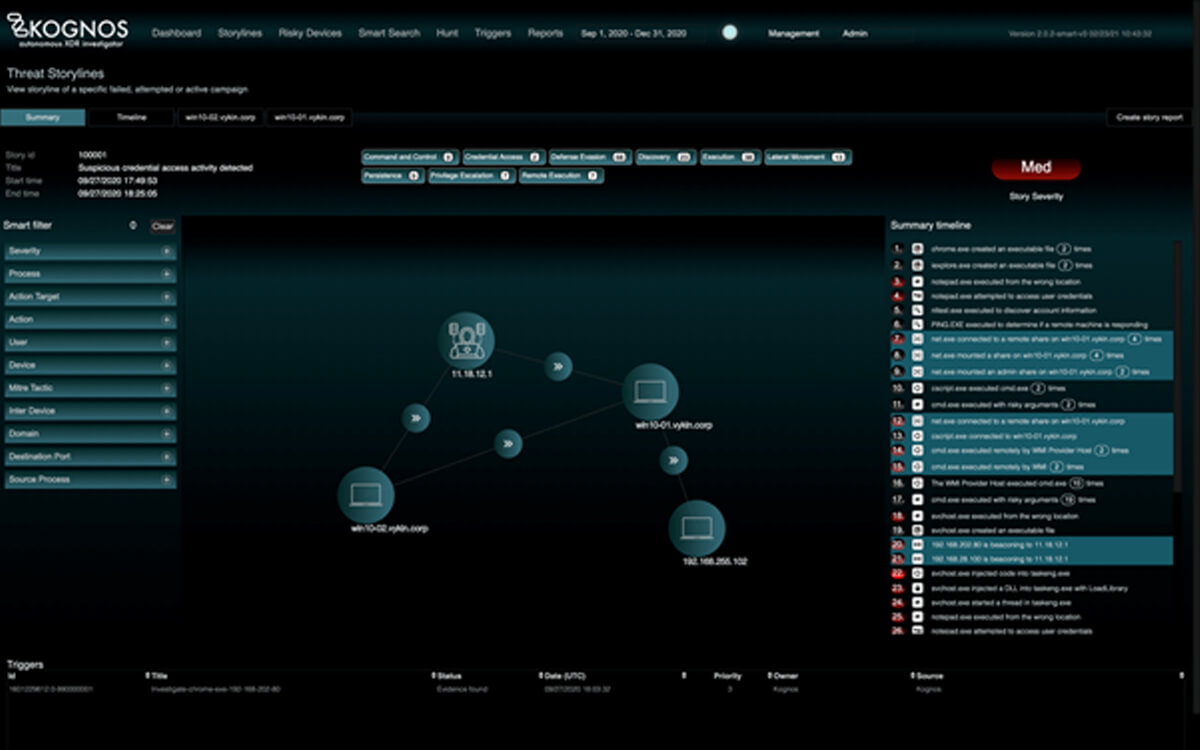
By autonomously forging relationships between event data coming from an organization’s existing telemetry sources, the Kognos XDR Investigator is the only solution that allows organizations to trace laterally moving campaigns, living off the land binaries, and insider threats–regardless of if they are active campaigns, attempted campaigns, or failed campaigns.
Laterally Moving Campaigns
Malicious actors are getting more sophisticated and are able to laterally move across an organization’s environment, making their campaigns difficult to detect from addressing alerts alone.
How Attacks Propagate:
These attackers typically enter the infrastructure using stolen credentials, phishing attacks, exploiting vulnerable servers, and establish a foothold in a handful of machines.
They are extremely stealthy and take their time:
- Doing reconnaissance
- Dumping credentials
- Escalating privileges
- Remaining hidden by employing various persistence mechanisms
As attackers collect more information and gain confidence with the infrastructure, they start laterally moving from machine to machine, using protocols like WMI, WinRM, Remote Desktop, etc. They continue to employ these techniques until they reach their desired outcome.