
AppWall – More Than Just a WAF
As cyberattacks and mitigation techniques continue to evolve, enterprises need to be on alert and keep time to protection as short as possible. Advanced methods

As cyberattacks and mitigation techniques continue to evolve, enterprises need to be on alert and keep time to protection as short as possible. Advanced methods
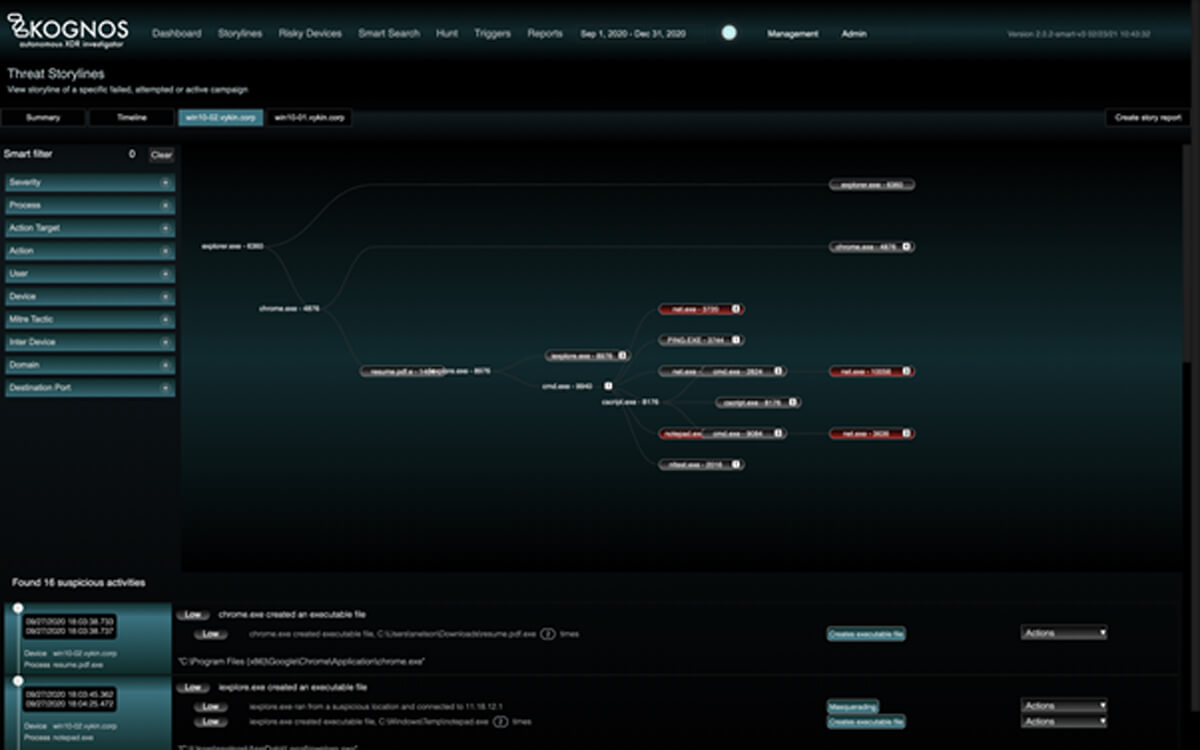
IDENTIFY ATTACKERS IN ACTION Attackers are becoming more sophisticated and the techniques they use are much stealthier, harder to detect, and take increasingly longer to
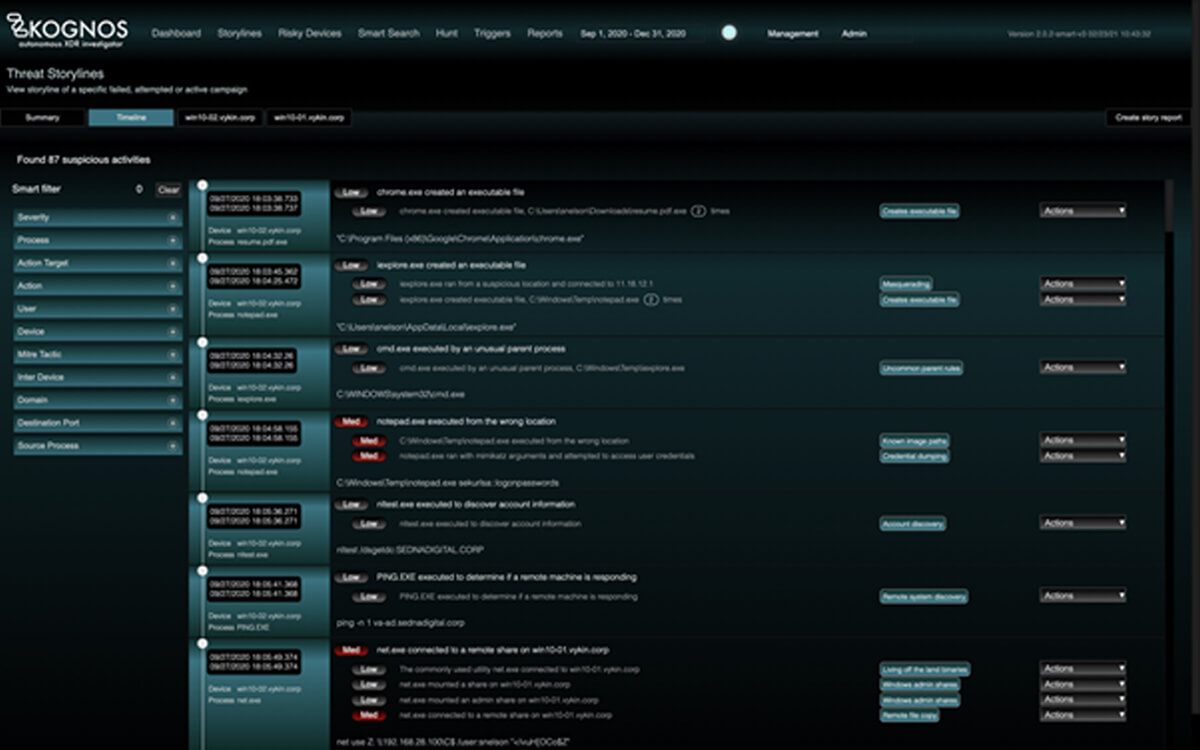
IDENTIFY ATTACKERS IN ACTION Attackers are becoming more sophisticated and the techniques they use are much stealthier, harder to detect, and take increasingly longer to
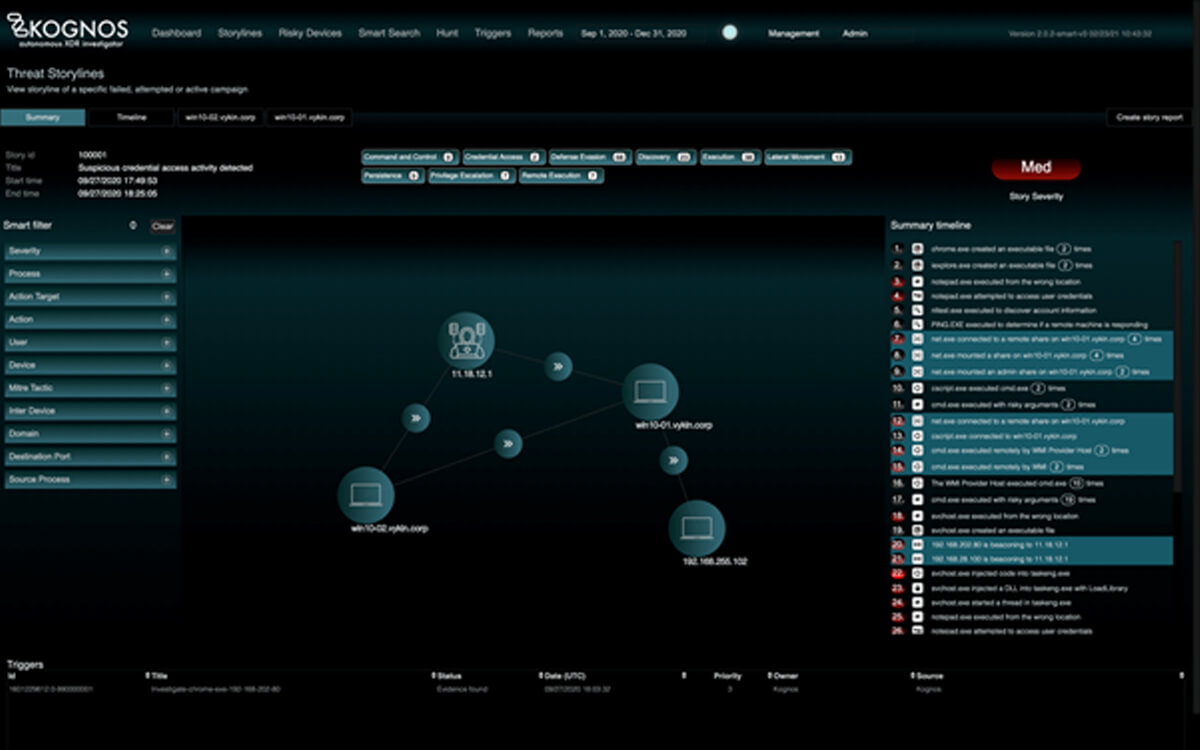
IDENTIFY ATTACKERS IN ACTION Attackers are becoming more sophisticated and the techniques they use are much stealthier, harder to detect, and take increasingly longer to

The introduction of XDR is a major evolution in understanding the effectiveness to threats within an organization. The threat data is available to Security analysts

As cyberattacks and mitigation techniques continue to evolve, enterprises need to be on alert and keep time to protection as short as possible. Advanced methods

IDENTIFY ATTACKERS IN ACTION Attackers are becoming more sophisticated and the techniques they use are much stealthier, harder to detect, and take increasingly longer to

IDENTIFY ATTACKERS IN ACTION Attackers are becoming more sophisticated and the techniques they use are much stealthier, harder to detect, and take increasingly longer to

IDENTIFY ATTACKERS IN ACTION Attackers are becoming more sophisticated and the techniques they use are much stealthier, harder to detect, and take increasingly longer to

The introduction of XDR is a major evolution in understanding the effectiveness to threats within an organization. The threat data is available to Security analysts
Join the Cyway community and get exclusive updates