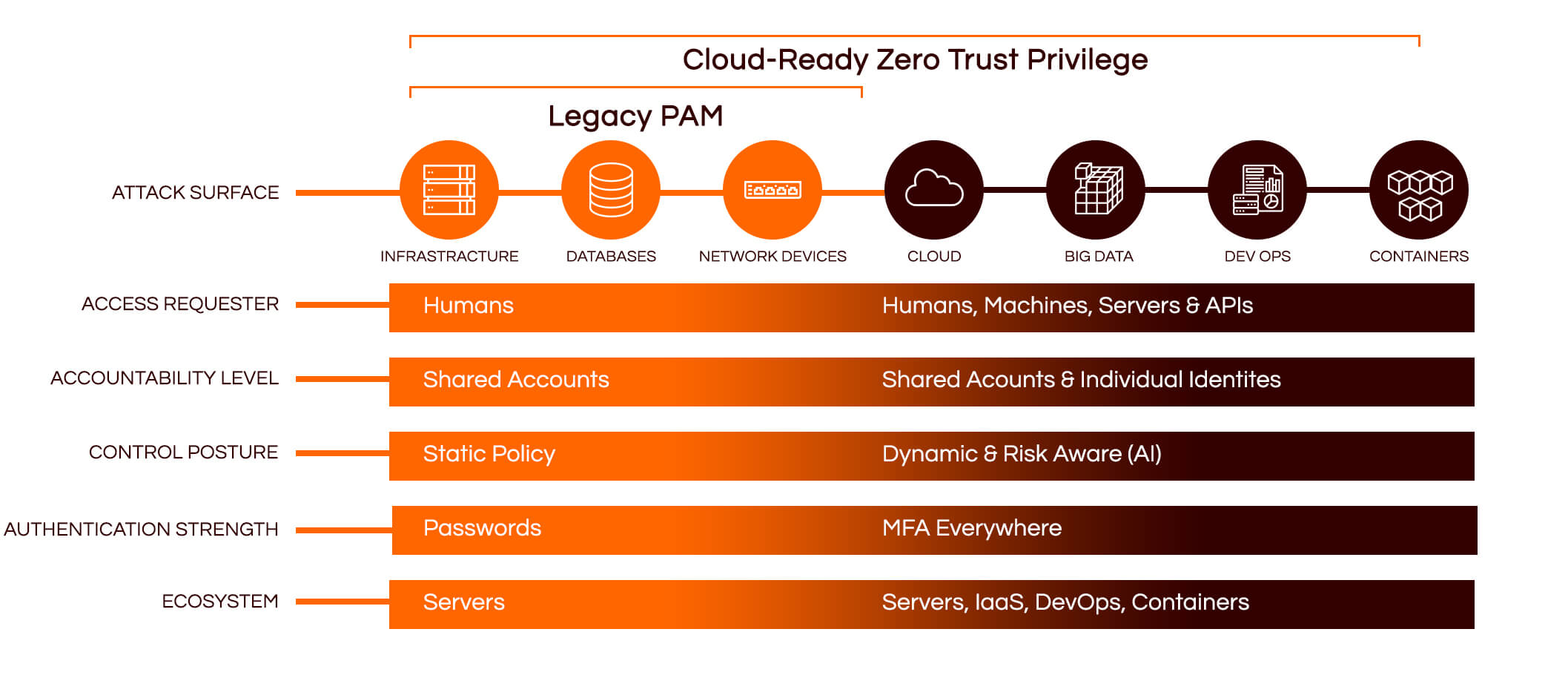
Legacy PAM has been around for decades and was designed back in the day when ALL your privileged access was constrained to systems and resources INSIDE your network. The environment was systems admins with a shared “root” account that they would check out of a password vault, typically to access a server, a database or network device. Legacy PAM served its purpose.
However, today’s environment is different, privileged access not only covers infrastructure, databases and network devices, but is extended to cloud environments. It also includes big data projects, it must be automated for DevOps, and it now needs to cover hundreds of containers or microservices to represent what used to be a single server.
On top of this, we now all live in a world of Advanced Persistent Threats (APTs) that create a growing and changing risk to organizations’ financial assets, intellectual property and reputations. Expanding access and obtaining credentials is an essential part of most APTs, with privileged access being the crown jewels.
Join the Cyway community and get exclusive updates